Scientific Research
-
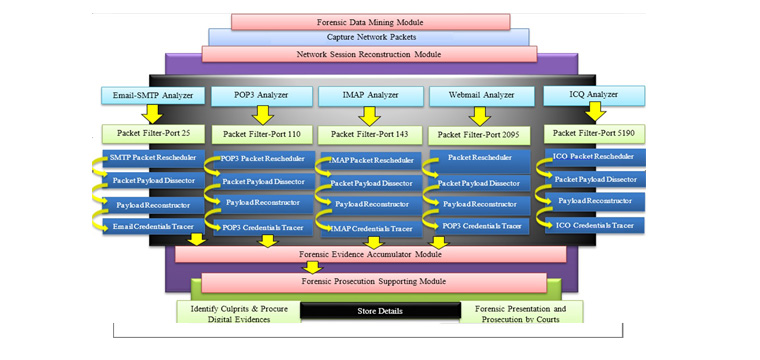
Network Forensic Investigation engine forf Email, Instant Messaging and Webmail and ICQ
-
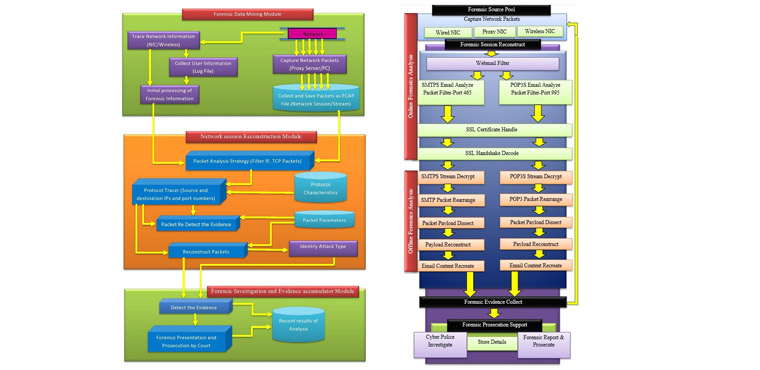
General Approach in adopted in Network Forensic Investigation
-
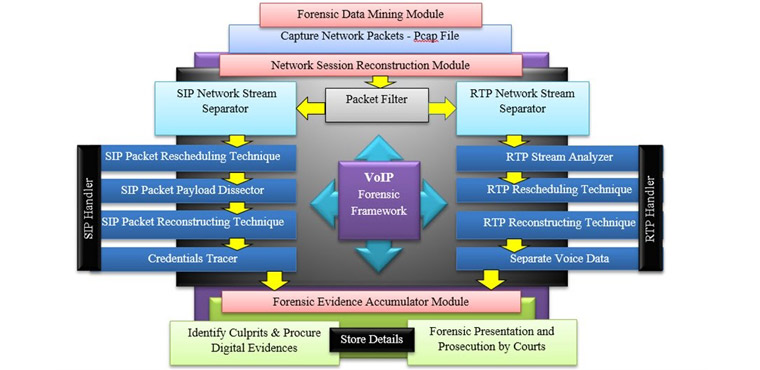
Forensic Framework for VoIP communication
This framework could reconstruct VoIP calls through a LAN or Wifi Enviornment
-
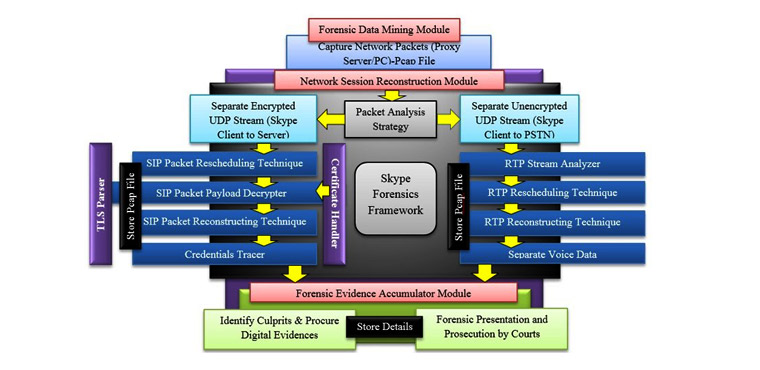
Forensic Framework for Skype communication
This framework could reconstruct Skype VoIP communication using codec G.729
-
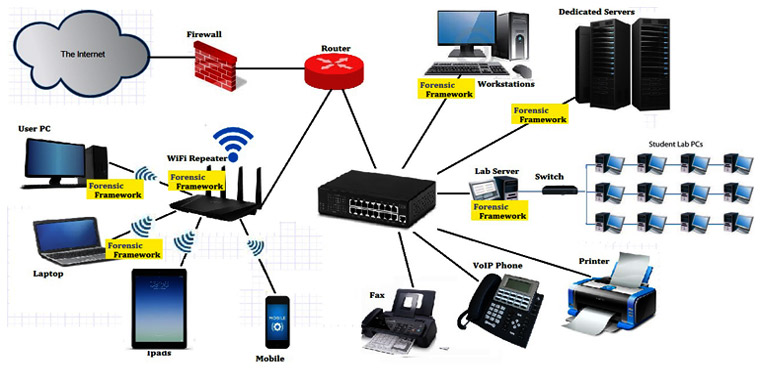
Model Computing Environment in my research works
Yellow colored points shows places where my forensic tools works
My researches are focused in the area of network and cloud forensic investigations. Currently developing a Forensic Investigation framework for cloud storage. My research areas also include SQL Injection Vulnerability Mitigation Techniques in Web Applications. Each of these research work is completed in the duration of 6 months to 1-year span. All these research works are funded by National Institute of Technology Karnataka, Adi Shankara Institute of Engineering and Technology, Cochin, Resource Center for Cyber Forensics, CDAC Trivandrum and Salman Bin Abdulaziz University, Kingdom of Saudi Arabia. I express my deep gratitude to respective authorities for providing infrastructure and fund to carry out and continue research work.
Listing of Research work’s Abstracts
-
- An Improved Approach towards Network Forensic Investigation of HTTP and FTP Protocols
-
- Network Forensic Investigation of HTTPS Protocol
-
- Forensic Investigation Framework for P2P Protocol
-
- Network Forensic Investigation of VoIP Protocol
-
- Forensic Investigation Framework for Tracing and Reporting Digital Crimes in Computer Networks
-
- A Method Of Detecting SQL Injection Attack To Secure Web Applications
-
- SQLStor: Blockage of stored procedure SQL injection attack using dynamic query structure validation
-
- SQL Injection Attack Solutions: A Review
-
- Image Authentication by Content Preserving Robust Image Hashing Using Local and Global Features
-
- Network Forensic Investigation of Skype Activities
-
- Level Based Anomaly Detection of Brain MR Images Using Modified Local Binary Pattern
-
- Denoising Multi-coil Magnetic Resonance Imaging using Nonlocal means on Extended LMMSE
-
- Email Forensics(Upcoming)
-
- Forensic Framework for Web services( Upcoming)
-
- Forensic Framework for google drive and Dropbox communications ( Upcoming)
- Mobile Android Forensic App ( Upcoming)
An Improved Approach towards Network Forensic Investigation of HTTP and FTP Protocols
Abstract. Network packet analysis and reconstruction of network sessions are more sophisticated processes in any network forensic and analysis system. Here we introduce an integrated technique which can be used for inspecting, reordering and reconstructing the contents of packets in a network session as part of forensic investigation. Network analysts should be able to observe the stored packet information when suspicious activity is reported and should collect adequate supporting evidence from stored packet information by recreating the original data/files/messages sent/received by each user. Thus suspicious user activities can be found by monitoring the packets in offline. So we need an efficient method for reordering packets and reconstructing the files or documents to execute forensic investigation and to create necessary evidence against any network crime. The proposed technique can be used for the content level analysis of packets passing through the network based on HTTP and FTP protocols and reports deceptive network activities in the enterprise for forensic analysis.
|
My contribution to Network Forensics:
-
- The proposition of an efficient algorithm for network packet reordering and reconstruction mechanism for handling packets which follow HTTP and FTP packets.
-
- Developed a module for HTTP and FTP packet dissection to retrace forensic information
- Proved that the proposed technique is well tuned and exhibits improved performance
|
|
Manesh, B. Brijith, and Mahendra Prathap Singh,”An Improved Approach towards Network Forensic Investigation of HTTP and FTP Protocols“, International Conference on Parallel, Distributed Computing technologies and Applications, Springer (Tirunelveli), September 2011
Forensic Investigation of Secure HTTP or HTTPS communications
Abstract – Nowadays a large amount of personal and business transactions are done electronically through secured internet communication with HTTPS Protocol. The internet offers computer users access to a wealth of information and reaches into the heart of many organizations. In this context, there are many possibilities for having different malicious activities or attacks that may occur through the HTTPS protocol. Usually, it is very difficult to see or recreate HTTPS network sessions to verify its content as part of the forensic analysis. Network analysts must be able to see and test the packet data when malicious network usage is identified and produce actual session by recreating the original data between users as part of forensic analysis. So we need an efficient forensic system to perform this kind of content analysis. The proposed novel technique can be used for content level observation of HTTPS protocol and regenerate original malicious HTTPS session between users for network forensic investigations.
[pdf]
Forensic Investigation Framework for P2P Protocol
Abstract-Online sharing of digital assets have now become common on the internet by its increased number of users over a decade drastically. There are many online sharing resources which offer huge storage. These facilities tend the internet users to upload and download pirated software, movies, and other similar digital assets which violates all copyrights. The P2P protocol is working behind such online sharing websites and resources. The cyber cell is very active now in various parts of the country to trace and fraudulent sharing of files when reported. So it is necessary to have an efficient mechanism to find the actual content which is being uploaded or downloaded from a particular machine as part of network forensic investigation. Usually, P2P websites and services are blocked in enterprises and educational institutions to avoid sharing of unwanted digital assets and also to increase internet bandwidth. The proposed novel technique is based on network forensics which can be used for content level observation of P2P Bit Torrent protocol and regenerate original malicious content or session between malicious users for their prosecution in the court.
T Manesh, “Forensic Investigation Framework for P2P Protocol“, International Conference on Control, Instrumentation, Communication, and Computational Technologies-2014, (July-2014)
[pdf]
Forensic Investigation Framework for VoIP Protocol
Abstract-The deployment of Voice over Internet Protocol (VoIP) in place of traditional communication facilities has helped in a huge reduction in operating costs, as well as enabled adoption of next-generation communication services-based IP. At the same time, cybercriminals have also started intercepting environment and creating challenges for the law enforcement system in any Country. At this instant, we propose a framework for the forensic analysis of the VoIP traffic over the network. This includes identifying and analyzing of network patterns of VoIP- SIP which is used for the setting up a session for the communication, and VoIP- RTP which is used for sending the data. Our network forensic investigation framework also focuses on developing an efficient packet reordering and reconstruction algorithm for tracing the malicious users involved in the conversation. The proposed framework is based on network forensics which can be used for content level observation of VoIP and regenerate original malicious content or session between malicious users for their prosecution in the court.
Forensic Investigation Framework for Tracing and Reporting Digital Crimes in Computer Networks
Abstract- Forensic investigation in computer networks is the process of capturing information that moves
over a network and trying to gather some forensic information from it and also called network .forensics. It is an art of discovery and retrieval of information about network events Present networks carry large volume of data as network packets, so managing the storage of packets, categorizing, analyzing and subsequent packet processing are found to be tedious .processes in forensic investigation This research work aims to introduce an integrated technique to be used for inspecting, reordering and reconstructing the contents of packets in a network session for forensic investigation of protocols for Email (SMTP, POP3 and IMAP), Webmail (Gmail and Yahoo), Chat and Instant Messaging (MSN, Google Talk and ICQ), Video upload and download stream using HTTP, Upload and download sessions using SFTP, Content retrieval from Skype . Conversation and VoIP protocols A typical network forensic investigation process should observe the stored packet information when suspicious activity is reported. The process should collect adequate supporting evidence from stored packets by recreating the original data, files, and messages sent or received by each user. Thus suspicious user activities can be found by monitoring the packets .in offline The proposed research work is also targeting in developing an efficient network packet reconstruction algorithm to execute forensic investigation activities and to create necessary evidence against any illegal network-related events. Hence the proposed methodology in this research project helps in content level analysis of packets passing through the network and reports any deceptive network activities in computing environments The expected experimental results of the proposed framework might improve performance of .network forensic investigation in terms of packet reordering and reconstruction time
A Method of Detecting SQL Injection Attack to Secure Web Applications
Abstract-Web applications are becoming an important part of our daily life. So attacks against them also increase rapidly. Of these attacks, a major role is held by SQL injection attacks (SQLIA). This paper proposes a new method for preventing SQL injection attacks in JSP web applications. The basic idea is to check before execution, the intended structure of the SQL query. For this, we use semantic comparison. Our focus is on stored procedure attack in which query will be formed within the database itself and so difficult to extract that query structure for validation.
Sruthy and Manesh T, “Method Of Detecting Sql Injection Attack To Secure Web Applications”, International Journal of Distributed and Parallel Systems (IJDPS) ,November 2012
[pdf]
Blockage of Stored Procedure SQL Injection Attack Dynamic Query Structure Validations
Abstract-Web applications play an important role in today’s business needs. There are huge number of websites which cater to different needs as web applications in the field of health care, IT consultancies, online shopping, Ticket Booking, Real Estate business, Bill payment etc. An important attack which make dangerous challenge in this services is SQL Injection Attack. This paper proposes a new method for preventing SQL injection attacks in web applications using SQL query structure validations. This method prevents different kinds of injection attacks including stored procedure attack which is more difficult and less considered in the literature.
Sruthy, Manesh T, Varghese Paul ” Blockage of stored procedure SQL injection attack using dynamic query structure validation “, 12th International Conference on Intelligent Systems Design and Applications (ISDA), 2012
SQL Injection Attack Solutions-A Review
Abstract— Web applications are becoming an important part of our daily life. So attacks against them also increase rapidly. Of these attacks, a major role is held by SQL Injection Attacks (SQLIA). This attack is launched through specially crafted user inputs and target web applications that used back end databases. Characteristics feature of this attack is that it will change the intended query structure. To avoid this type of attack, the best solution is to do not allow the user to enter any part of the SQL query directly. In this paper, we describe SQL Injection attack, various types and a detailed review of its solution techniques.
Sruthy, Manesh T, Varghese Paul, ” SQL Injection Attack Solutions: A Review“, International Journal of Scientific & Engineering Research, August 2013
[pdf]
Image Authentication by content preserving Robust Image Hashing using Local and Global features
Abstract -Image hashing is an authentication technique which constructs a short sequence from the image to represent its contents. This method proposes an image hash which is generated from local features such as Haralick features and MOD-LBP features and global features such as luminance and chrominance characteristics of the image which are computed from Zernike moments. Sender generates the hash from image features and attaches it with the image to be sent. The hash is analyzed at the receiver to examine whether the image is authentic or not. The proposed method detects image forgery and locates the forged regions of the image. The proposed hash is robust to common content preserving modifications such as JPEG image compression, the addition of noise, brightness and contrast adjustments, scaling, slight rotation and small cropping and it is sensitive to malicious manipulations. The performances of the hashes generated from each local feature combined with global features and both local features combined with global features are analyzed.
Forensic Framework for Skype Communication
Abstract -Skype is a secure internet telephonic application which establishes connection between its clients through a peer-to-peer architecture. The connection between Skype client to its server and other clients uses an encrypted channel that uses Transport layer Security (TLS) protocol. At the same time, connection between Skype client and Public Switch telephone Network (PSTN) gateway is accomplished through unencrypted digital channel using Voice over Internet
Protocol (VoIP). The encrypted channels in the Skype communication make forensic analysis frameworks to work badly in decrypting the traffic and procuring critical forensic details of the network stream against intruders and cyber criminals. Furthermore, policy violations and unbound usage of Skype VoIP communication over PSTN users waste the network bandwidth. Here we propose a sophisticated Skype forensic framework that collects forensic information by decrypting the Skype client-server communication along with recreating voice content in the Skype to PSTN VoIP communication. We also propose an efficient packet reconstruction algorithm powered by time stamping technique for regenerating malicious content from payloads of the Skype network stream followed by supporting prosecution of policy violators and cyber criminals in the court of law.
Level Based Anomaly Detection of Brain MR Images Using Modified Local Binary Pattern
Abstract -Medical imaging technology plays a crucial role in the visualization and analysis of the human body with unprecedented accuracy and resolution. Analyzing the multimodal for disease-specific information across patients can reveal important similarities between patients, hence their underlying diseases and potential treatments. Classification of MR brain images as normal or abnormal with information about the level at which it lies is a very important task for further processing, which is helpful for the diagnosis of diseases. This paper focuses on the abnormality detection of brain MR images using search and retrieval technique performed on similar anatomical structure images. Similar anatomical structure images are retrieved using the Modified Local Binary Pattern (MOD-LBP) features of the query and target images and the level of the image is identified. The query image is compared with images in the same level and classification is done using the SVM classifier. The result reveals that the classification accuracy is improved significantly when the query image is compared with similar anatomical structure images.
Denoising Multi-coil Magnetic Resonance Imaging using Nonlocal means on Extended LMMSE
Abstract -Denoising plays a key role in the field of medical images. Reliable estimation and noise removal is very important for an accurate diagnosis of the disease. This should be done in such a way that original resolution is retained while maintaining the valuable features. Multi-coil Magnetic Resonance Image(MRI) trails nonstationary noise following Rician and Noncentral Chi(NC-c) distribution. On using the modern techniques which make use of multi-coil MRI like in GRAPPA would yield nc-c distributed data. There has been lots of research done on the Rician nature but only a few for nc-c distribution. The proposed method uses Nonlocal Mean(NLM) on extended Linear Minimum Mean Square Error(ELMMSE) for denoising multi-coil MRI having nc-c distributed data. The performance of the nonlocal scheme on multi-coil MRI is evaluated based on PSNR, SSIM, and MSE and the result indicates proposed scheme is better than the existing scheme including Nonlocal Maximum Likelihood(NLML), adaptive NLML and ELMMSE.
VoIP Forensic Analyzer
Abstract -People have been utilizing Voice over Internet Protocol (VoIP) in most of the conventional communication facilities which have been of assistance in the enormous attenuation of operating costs, as well as the promotion of next-generation communication services-based IP. As an intimidating upshot, cybercriminals have correspondingly started interjecting the environment and creating new challenges for the law enforcement system in any Country. This paper presents an idea of a framework for the forensic analysis of the VoIP traffic over the network. This forensic activity includes spotting and scrutinizing the network patterns of VoIP-SIP stream, which is used to initiate a session for the communication, and regenerate the content from VoIP-RTP stream, which is employed to convey the data. Proposed network forensic investigation framework also accentuates on developing an efficient packet restructuring algorithm for tracing the depraved users involved in a conversation. Network forensics is the basis of proposed work, and performs packet level surveillance of VoIP followed by reconstruction of original malicious content or network session between users for their prosecution in the court.
Manesh T, Mohammed. ” VoIP Forensic Framework” published in International Journal of Advanced Computer Science and Applications (ISI Thomson Reuters indexed), Vol 1, Issue 1, Feb 2016
Forensic Investigation Framework for VoIP Protocol
Abstract -The deployment of Voice over Internet Protocol (VoIP) in place of traditional communication facilities has helped in a huge reduction in operating costs, as well as enabled adoption of next-generation communication services-based IP. At the same time, cybercriminals have also started intercepting environment and creating challenges for the law enforcement system in any Country. At this instant, we propose a framework for the forensic analysis of the VoIP traffic over the network. This includes identifying and analyzing of network patterns of VoIP- SIP which are used for the setting up a session for the communication, and VoIP RTP which is used for sending the data. Our network forensic investigation framework also focuses on developing an efficient packet reordering and reconstruction algorithm for tracing the malicious users involved in the conversation. The proposed framework is based on network forensics which can be used for content level observation of VoIP and regenerate original malicious content or session between malicious users for their prosecution in the court.













